How Does Role-Based Access Control Work in Headless CMS?

What’s Inside
- What Is RBAC (Role-Based Access Control)?
- What Is the Importance of Role-Based Access Control for Your Organization?
- Take Control of Your Organization's Digital Security with Role-based Access Control
- RBAC Best Practices to Ensure Efficient Results for Your Organization
- Use Cases of Role-Based Access Control in Various Industries
- Take Charge to Protect Organization's Sensitive Data with RBAC
- Experro Headless CMS’s Exclusive RBAC (Control Access) Capabilities
- Enforce Robust Security, Collaborate Effectively, and Improve Workflow with RBAC
- Conclusion
Summary
- Protecting sensitive data is of utmost importance in organizations.
- Role-based access control (RBAC) in headless CMS acts as a security shield against unauthorized access.
- RBAC systems offer pre-defined roles, streamlining data access management.
- This blog dives deep into the nuances of RBAC and its growing relevance in today's organizations using headless CMS.
Did you know? 49% of tech employees admit they have been involved in data breach activity while leaving or after being dismissed from the job! The sensitive information of organizations is constantly under threat. More than ever, it’s time to take robust security measures now!
However, beyond fostering security, organizations seek to streamline operations, maximize efficiency and reduce administrative work.
Enter role-based access control (RBAC) - the superhero solution! With RBAC in action, organizations can embrace efficiency like never before.
Picture role-based access control as a traffic light signal on a bustling highway! Just like traffic lights prevent some cars from going ahead for better security, RBAC regulates role-based access permissions in a digital realm.
In this blog post, we will delve into the remarkable capabilities of Role-Based Access Control (RBAC) of headless CMS and explore its diverse advantages to organizations.
What Is RBAC (Role-Based Access Control)?

RBAC meaning: Role-based access control, provides access permissions based on the roles and responsibilities of individual users within an organization. It restricts system access to unauthorized entities.
Here role assignments are defined by job function, responsibility, and authority level in the organization. The required role is given control access to the website's backend or specific resources. Let's understand from the example of the content writer.
Role: Content writer.
Responsibility: Writing and managing digital content.
Access control: Access to specific documents to read, write, and edit content.
The user permissions that RBAC restricts are:
- Sensitive data and information
- System access and applications
- Administrative functions
- Network access
What Is the Importance of Role-Based Access Control for Your Organization?

RBAC is important for organizations to enable security and streamlined control access. It ensures employees only have access to resources based on their roles and responsibilities.
While granting permission is crucial, it is equally important to recognize that unauthorized access can be misused.
From the points mentioned below, let’s determine the importance of role-based access control:
1. Providing Robust Security
You will be surprised to know that 60% of data breaches are caused by insider threats.
Insider threats are the sensitive data leakages caused by the present or former individuals of the organizations.
Since data leakage leads to financial consequences and reputational loss, it is imperative to protect sensitive data. RBAC system follows the principle of least privilege, it includes restricting access to the resources that are not required to perform job tasks.
Furthermore, customers too are cautious about their sensitive data information these days. So, providing robust security to your organization with RBAC will foster customer trust and increase the organization’s credibility.
2. Enables Simplified Management
RBAC architecture provides a centralized method for managing access-based roles and permissions. By utilizing RBAC, organizations can streamline granting or revoking employee access rights.
This includes revoking unnecessary access rights from the outgoing employee and granting access permissions to the new joiner.
Compared to manual methods, which are time-consuming and prone to errors, RBAC significantly handles these tasks and saves time and effort. Moreover, role-based access control unifies employee experience while working and reduces administrative overhead tasks.
Also read - DXP Architecture Explained!
3. Improved Productivity and Efficiency of Employees
A total of 92% of employees say that their work satisfaction is significantly impacted by the technology they use. Through RBAC, user role and permission are pre-defined. It eliminates the need for existing employees to request access to each task individually.
Since employees can quickly access the resources and tools, they need to perform specific tasks, it increases their productivity. This streamlines their work process and reduces delays in delivering assigned tasks.
4. Empowering Employee Collaboration
"Great things in business are never done by one person. They're done by a team of people."
- Steve Jobs
The above words emphasize the impact of employees' collective efforts on the organization’s success. Fostering collaboration within the organization harnesses the power of collective intelligence and leverages employees’ unique strengths.
Role-based access control manages access rights of employees to share document access within an organization to collaborate. Moreover, RBAC enables temporary access to third-party users to access role-based permissions to external stakeholders or clients. It ensures that sensitive data remains secure.
5. Maintaining Transparency Within the Organization
User access to resources is pre-defined and tied to specific roles; thus, it maintains transparency in collaboration. RBAC enables organizations to deny access to unauthorized users, mitigating the risks of misuse or information leaks.
With pre-defined roles, it becomes easier to monitor and identify if users have accessed specific operating systems or information beyond their permission. This tracking capability encourages employees to adhere to ethical practices and maintain transparency within the organization.
RBAC Best Practices to Ensure Efficient Results for Your Organization

Before implementing role-based access control through headless CMS, you must follow the best practices to ensure efficient results.
Go through the points mentioned below to understand best practices of RBAC:
1. Define Clear Roles and Permissions
It is necessary to define roles and permissions while deciding the RBAC. It includes first identifying users' job roles, functions, and duties and then defining user privileges for them. Defining roles and permissions properly contributes to the overall security and effectiveness of access control.
With clearly defined roles and permissions, your users will only have access to necessary resources and nothing more!
Let us understand this with an example:
For instance, in an advertisement enterprise, roles include marketing managers, content creators, designers, social media strategists, and sometimes even an external ghost writing service.
Marketing managers have access to campaign resources and budget documents, while content writers and designers have permission to edit and collaborate on those documents.
2. Review and Update Access Rights
Reviewing and updating access rights is important to regulate role-based access control.
In the scenario where employees change their organizational roles, it becomes essential to review and update access rights as per the allotted roles and responsibilities.
Similarly, if employees leave the organization, their access privilege should be revoked to secure the data. Reviewing and updating access rights adds an additional effort to securing data.
3. Enforcing Authentication Mechanism
Enforcing an authentication mechanism is crucial to verify user identity. This involves providing employees with unique usernames and passwords to verify the user before granting access.
Two-factor authentication is also a popular way to verify user identity. By enforcing a strong mechanism, organizations can ensure that only authorized users can access the information.
Use Cases of Role-Based Access Control in Various Industries
Role-based access control is a versatile model that can be used across various industries and companies.
Here we have listed a few of the examples where it has been widely used:
RBAC Use in eCommerce Industry
In the eCommerce industry, RBAC model entails an access control method for various roles. As eCommerce generally contains a huge catalog and customer information database, it is crucial to determine clear roles and permissions.
Let's understand from the example of a store manager:
Role - eCommerce store manager.
Responsibility - Managing operation of eCommerce store, customer orders, and product inventory.
Access control - eCommerce platform, customer database access, and inventory management system.
RBAC Use in Educational Websites
Implementing RBAC model plays a vital role in educational websites by defining robust access control for various roles.
Let's understand from the example of the course instructor:
Role - Course instructor
Responsibility - Creating course content, communicating with students.
Access control - Access course materials and student data to perform system maintenance while limiting access for other roles.
RBAC Use IT Companies
In IT services, RBAC serves as a fundamental model for securing data and providing mandatory access control to roles.
Let’s understand from the example of an IT administrator:
Role - IT Administrator
Responsibility - Managing IT infrastructure, ensuring system security, and providing technical support.
Access control - Resources such as server administration tools, network devices, and user accounts to perform technical tasks.
RBAC Use in Financial Institutions
RBAC provides access controls to trading platforms, granting traders and brokers the necessary permissions to execute trades, monitor market data, and manage client portfolios.
Let's understand the role of a financial analyst:
Role - Financial Analyst
Responsibility - Conducting financial analysis, preparing reports, and providing investment recommendations.
Access control - Financial data, investment platforms, and risk management systems.
RBAC Use in Advertisement Agency
RBAC in advertisement agencies can allocate roles for social media managers with access to client accounts and marketing campaigns.
Let’s understand with the example of social media manager:
Role - Social Media Manager
Responsibility - Managing social media accounts, creating content, and engaging with the audience.
Access control - Social media platforms, content management tools, and analytics.
Experro Headless CMS’s Exclusive RBAC (Control Access) Capabilities
Experro is a leading headless CMS platform that aligns with the modern digital landscape and aims to elevate organization’s efficiency. Enhancing role-based access control capabilities is one of the significant advantages of Experro’s headless CMS.
Follow the headless CMS guide blog to get more insights about what is headless CMS and how to use it for one site or multiple sites.
Managing roles in headless CMS becomes crucial to streamline workflow. Experro headless CMS enables assigning specific roles and permissions to different users and simplifies content management with RBAC.
Moreover, Experro allows organizations to edit roles and permissions according to changing requirements of the organization.
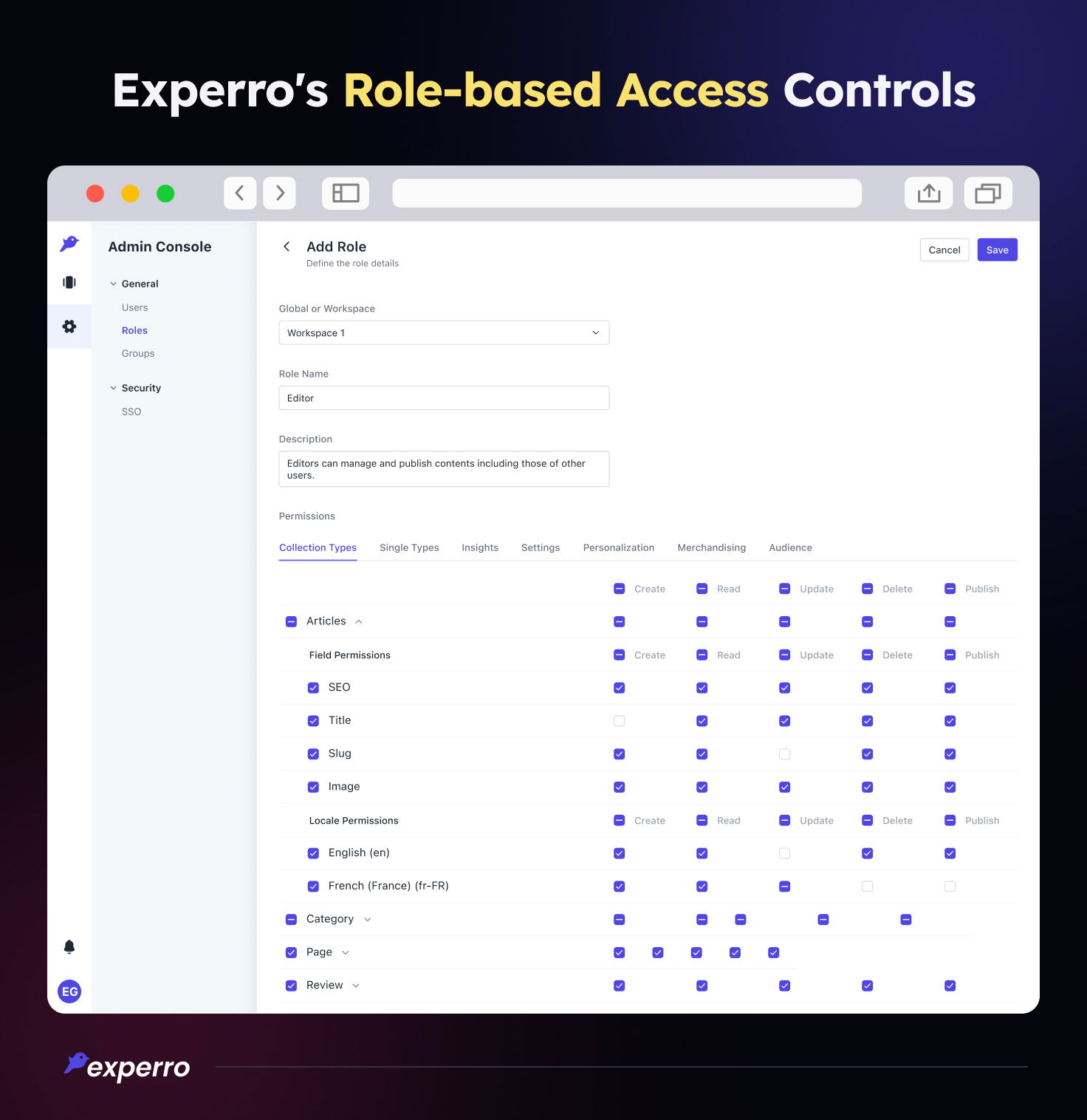
What More Can You Expect from Experro’s Headless CMS?
Experro’s headless CMS is coming up soon with an exclusive workflow management and approval feature. It will enable organizations to define and automate workflow management.
Conclusion
Enabling role-based access control by best headless CMS ensures security regulation and granular control over user permissions. RBAC not only provides robust security but also streamlines content creation and publishing workflows. To unlock these benefits for your organization, book a demo now with Experro!
FAQs


Priya Zala
14 June 2024Through her writing, she has a lovely way of capturing users' pain points and delivering solution-oriented content. Her writing is sure to captivate readers and leave them with a lasting impression. When not crafting content, Priya enjoys getting lost in a good work of fiction, which soothes her soul.